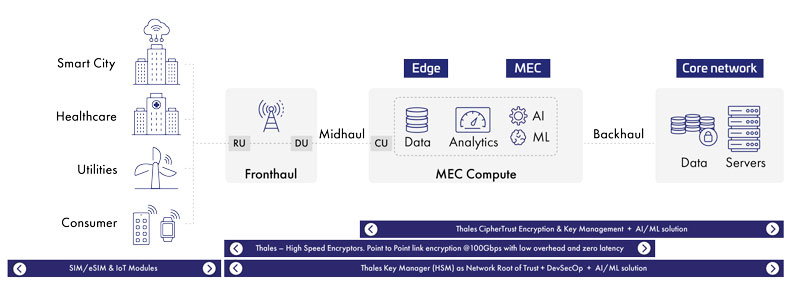
5G Security Solutions for Protecting Point-to-Point Network Links
In the past, networks were mostly hardware-based. However, 5G enables a much broader array of connections, including:
- Hardware communicating with virtual machines.
- Virtual machines communicating with virtual machines.
- Virtual machines communicating with containers.
- Containers communicating with containers, and so on.
Thales data in motion security solutions enable Mobile Network Operators to overcome those obstacles by maximizing 5G security without compromising performance, with low latency, near-zero jitter, and high throughput.
Thales High Speed Encryptors are specifically designed to protect data in motion. They work in Open System Interconnection (OSI) layers 2, 3, and 4 and are three times faster and deliver much lower latency than IPSec. They can be deployed either as hardware or virtual appliances and are FIPS 140-2 level 3, Common Criteria, NATO, and UC APL certified. Our High Speed Encryptors also integrate with quantum security solutions, ensuring relevance for years to come.